Οι πολιτικές πρόσβασης υπό όρους στην απλούστερή τους είναι οι δηλώσεις if-then, εάν ένας χρήστης θέλει να αποκτήσει πρόσβαση σε έναν πόρο, τότε πρέπει να ολοκληρώσει μια ενέργεια. Παράδειγμα: Ένας διαχειριστής μισθοδοσίας θέλει να αποκτήσει πρόσβαση στην εφαρμογή μισθοδοσίας και απαιτείται να πραγματοποιήσει έλεγχο ταυτότητας πολλαπλών παραγόντων για πρόσβαση σε αυτήν.
Οι διαχειριστές αντιμετωπίζουν δύο πρωταρχικούς στόχους:
- Να ενδυναμώνουν τους χρήστες να είναι παραγωγικοί οπουδήποτε και όποτε
- Να προστατέυουν τα assets του οργανισμού.
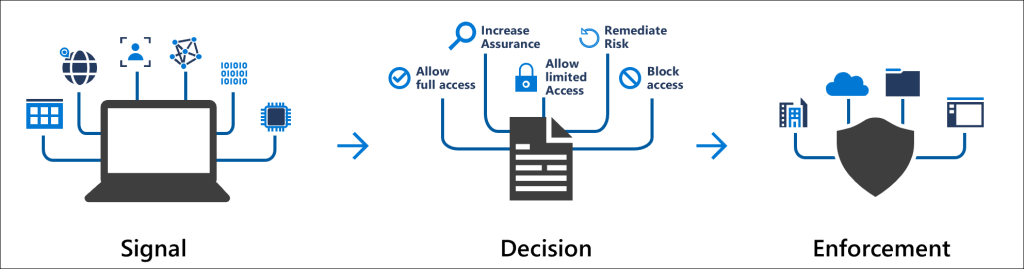
Use Conditional policies to apply the right access controls when needed to keep your organization secure.
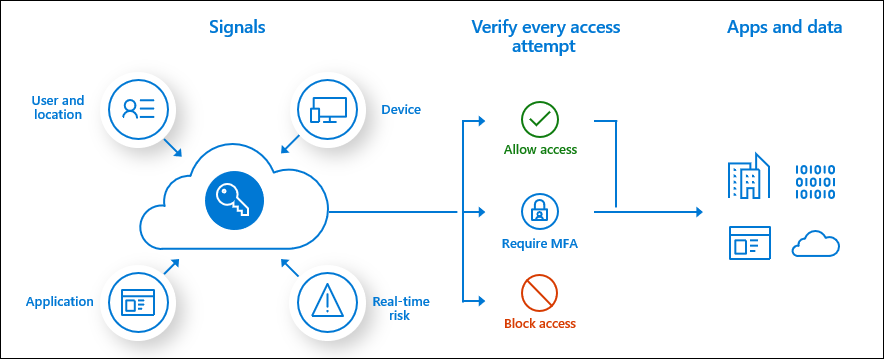
Technical Aspects
One of the core technical aspects is the contextual enforcement of policies. CA evaluates a wide array of signals such as user identity, device compliance, location, and application being accessed. For instance, administrators can create policies that require multi-factor authentication (MFA) if a user is attempting to sign in from an unfamiliar location or using a non-compliant device. This dynamic enforcement allows organizations to strike a balance between security and user convenience, ensuring access is granted based on risk level rather than blanket restrictions.
Another technical feature of Entra ID Conditional Access is the granular control over access scenarios. Administrators can set policies not only based on user and device signals but also tailored to specific applications and session controls. For example, policies can restrict access to sensitive applications unless certain conditions are met, such as being on a corporate network or using a trusted device. Session controls, like “app-enforced restrictions” or “conditional access app control,” enable further refinement by limiting users’ ability to perform specific actions within applications (e.g., downloading files in unmanaged devices). This fine-tuned approach ensures that the right level of security is applied across varying access scenarios, protecting corporate resources while allowing flexibility for different use cases.
Summary
Conditional Access offers several advantages, including enhanced security through real-time risk-based access controls, improved user experience by dynamically enforcing policies only when necessary, and granular control over application and session access. These capabilities help organizations protect sensitive resources while maintaining flexibility and efficiency in user access management.
